TrustPath + Kinde: Prevent Fraud with Secure Authentication
Enhance authentication security by integrating TrustPath's fraud detection with Kinde. Prevent account fraud while maintaining seamless user experience.
So much of our financial and administrative lives are online, making the need for strong account security more critical than ever. Fraudulent account creation and account takeovers (ATOs) are on the rise, often driven by tactics like disposable emails, credential stuffing, and automated bot attacks. Businesses need to take proactive measures to maintain customer trust and protect user data.
TrustPath.io's fraud detection API helps enhance authentication workflows by identifying suspicious activity at sign in and registration. When combined with Kinde's authentication platform, you'll be able to create a seamless and highly secure experience, preventing fraudulent access while ensuring legitimate users can authenticate effortlessly.
But what is it that we need to guard against?
Common threats to account security
Fraudsters continuously evolve their tactics, using techniques like disposable emails, credential stuffing, and automated bots to bypass traditional safeguards. By analyzing risk signals in real-time, businesses can prevent fraudulent activity without disrupting the experience for legitimate users.
Here are some typical threats that organizations face.
- Fake account creation: Fraudsters generate fake accounts using temporary emails and automated tools, often to exploit promotions, spread spam, or conduct fraudulent activities.
- Account Takeover (ATO): Cybercriminals attempt to gain unauthorized access to real user accounts through credential leaks, phishing, or brute-force attacks, leading to financial fraud and data breaches.
- Account sharing: Though not always fraudulent, account sharing can pose security, compliance, and revenue risks. Detecting shared accounts helps enforce policies and protects user data.
Kinde's authentication and access control offers a strong foundation for securing user access, but integrating fraud detection adds another critical layer of protection.
How TrustPath checks authentication in Kinde
One of Kinde's workflow triggers is called user:post_authentication. This trigger fires after the user successfully signs in, making it an ideal point to send a request to TrustPath's fraud detection API.
Here's how it works:
- A user registers or signs in to your application. This activates the
user:post_authenticationtrigger in Kinde, initiating the workflow. - The workflow sends the user's auth details (email, name, IP, etc.) via the Kinde Management API to TrustPath's API.
- TrustPath then evaluates the event, calculates a risk score and provides a state back to Kinde via the workflow.
- Based on the returned state, you can allow or deny access, or note the authentication event for further review.
Understand TrustPath evaluation methods
Once integrated into your Kinde workflow, TrustPath evaluates every sign in attempt using a layered, real-time risk assessment. Here's what that process looks like:
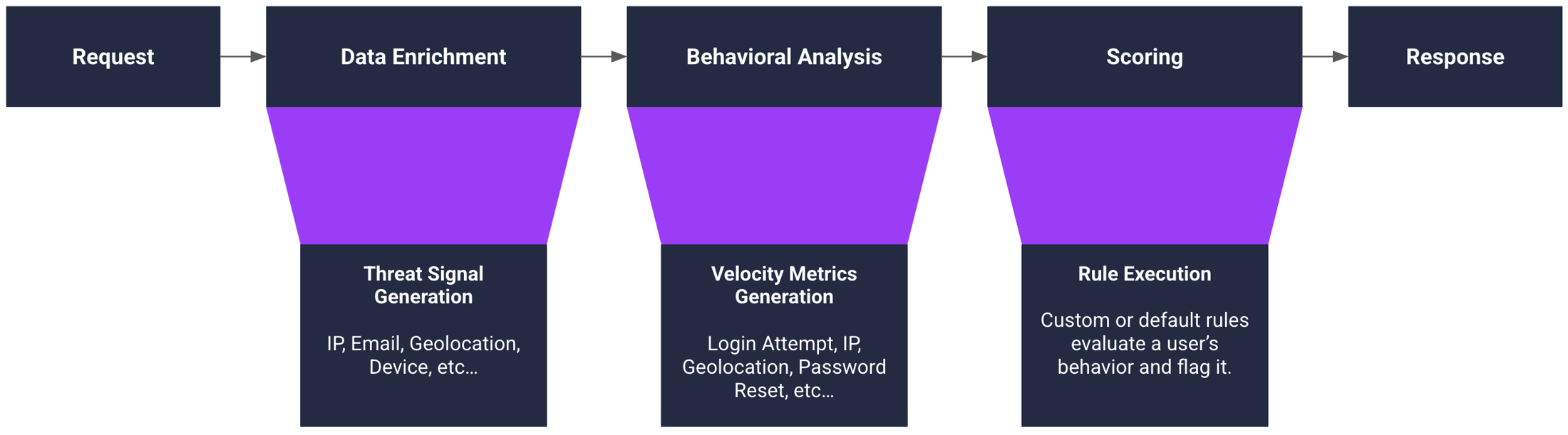
Threat analysis can include:
Email Intelligence - Detects risky or disposable email addresses commonly used in fraudulent registrations.
IP Intelligence - Analyzes IP addresses and geolocation data to flag unusual access patterns, such as use of proxies, VPNs, or known abusive IP ranges.
Device Intelligence - Uses device fingerprinting and browser analysis to uncover suspicious behavior like rapid device switching or automation.
Behavioral Analysis - Monitors user behavior over time to detect anomalies such as unusual login velocity, inconsistent interaction patterns, or session hijacking.
Custom Rules - You can tailor detection thresholds and responses to your platform's needs—for example, bypassing checks for internal testers or automatically blocking traffic from specific regions.
Risk Scoring - Each login attempt receives a dynamic risk score based on combined data points. This score informs whether to allow access, block the attempt, or trigger step-up authentication (e.g. additional verification).
Understand Kinde workflows
A Kinde workflow is a series of actions executed based on your code when an event trigger fires.
The best part of the feature is that Kinde connects to your own Git repo, so you can store and design your workflow code on familiar territory. When a Kinde workflow runs, your code is executed. Or in the case of an integration with TrustPath, a threat analysis is initiated.
Here's the Kinde docs for learning more about workflows.
Manage allow & deny lists in TrustPath
As part of threat management, TrustPath lets you use allow and deny lists for specific users, emails, IPs, or devices.
- Allow List: Designate trusted users, domains, or IPs to reduce false positives and streamline authentication.
- Deny List: Block known fraudulent entities, such as disposable emails, high-risk IPs, or repeat offenders, to prevent unauthorized access.
These lists can also be used for testing specific use cases or immediately allowing or blocking certain threats, giving you greater flexibility in managing authentication security.
By integrating allow and deny lists within Kinde's authentication flow, businesses can enhance security while maintaining a seamless user experience.
Get started
Follow the Integration guide to set up fraud detection with TrustPath.
Watch a demo
Support
Follow the provided guide to integrate TrustPath.
If you need extra support, here's where to get it.
- TrustPath.io Support: For questions related to fraud detection rules, API integration, or threat analysis, visit TrustPath.io or contact our team at trustpath.io/contact or support@trustpath.io , for API documentation docs.trustpath.io
- Kinde Support: For help with authentication workflows, triggers, or general setup, refer to the Kinde Documentation or reach out to Kinde's support team.
Kinde is an authentication provider based in Australia, serving customers worldwide. TrustPath wrote this article in collaboration with the Kinde team - you can read the original article on Kinde's blog.