Auto-Defense
Automated protection against suspicious activities with intelligent blocking mechanisms based on behavioral patterns and device fingerprinting.

Use Case
Stop unauthorized credential sharing and protect your subscription-based services from account abuse with advanced fingerprinting technology
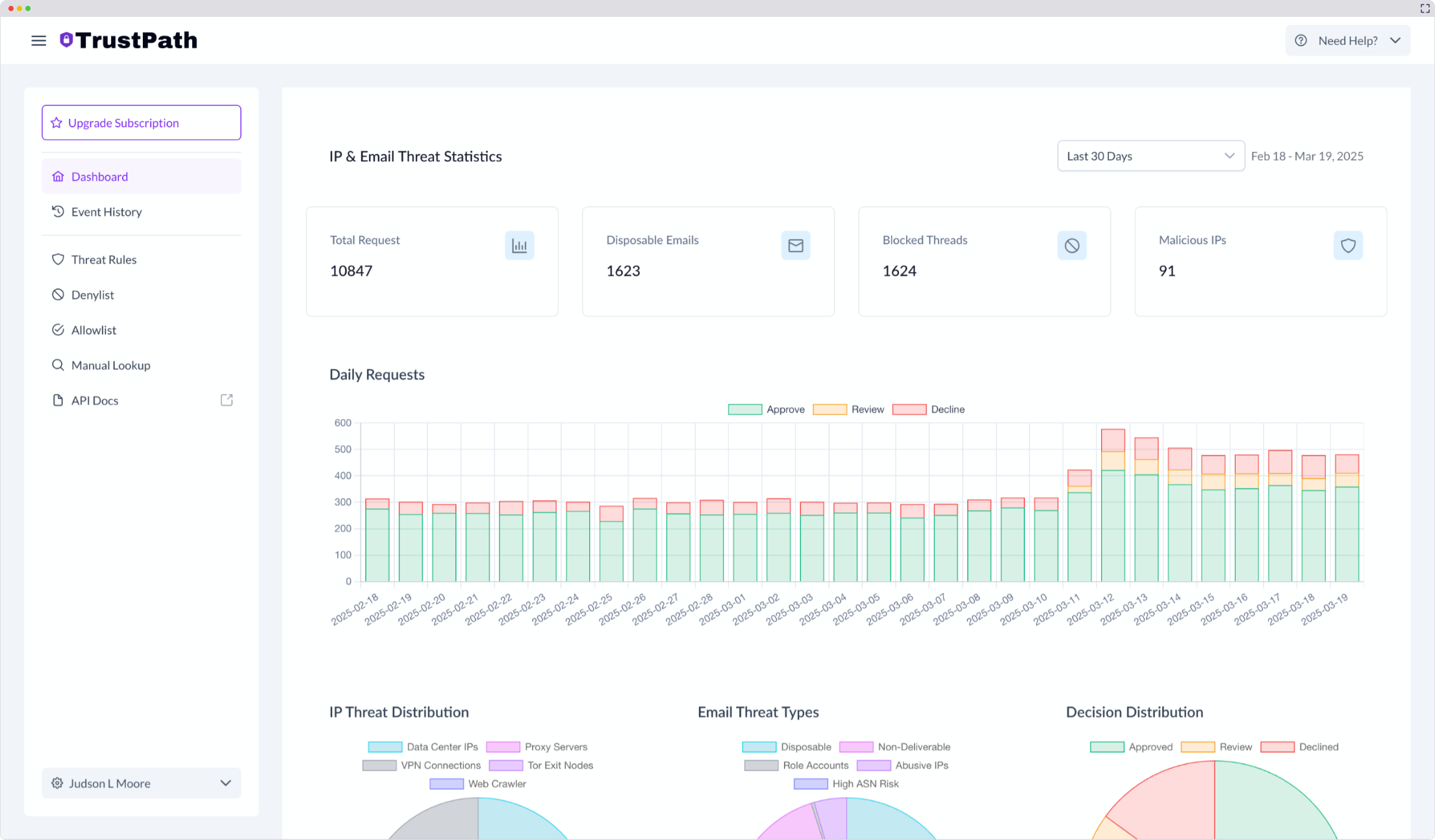
OUR TECHNOLOGY
Real-time transaction monitoring and risk assessment.
Fraud pattern recognition and behavioral analysis.
Automated blocking of suspicious transactions while allowing legitimate ones.
Stop Unauthorized Credential Sharing
Credential sharing undermines revenue models, violates terms of service, and can lead to service degradation for legitimate users.

Identify when the same account is being used from multiple devices or locations simultaneously.
Accurately identify unique devices even when users attempt to mask their identity.
Enforce usage limits and fair access policies based on legitimate usage patterns.
Explore the solutions that help address this challenge.
Automated protection against suspicious activities with intelligent blocking mechanisms based on behavioral patterns and device fingerprinting.
Advanced device fingerprinting technology to identify and track devices across sessions and detect suspicious behavior patterns.
Advanced behavioral analysis to detect unusual user patterns and identify potential fraud based on user interaction and behavior.
Comprehensive device intelligence to understand user behavior patterns and detect anomalies across different devices and platforms.
Advanced IP analysis and intelligence to identify and block malicious connections and suspicious network activity.
Comprehensive risk scoring system to evaluate and quantify potential threats and provide actionable risk assessments for fraud prevention.
Trust
We maintain high security standards and aim to comply with major industry regulations and frameworks.



Schedule a demo with our fraud prevention experts to see how TrustPath can secure your transactions. Get personalized insights into your specific fraud risks.
Engin Yöyen
Co-Founder